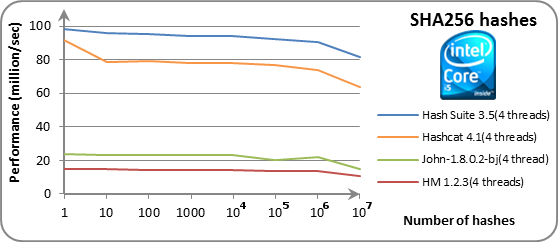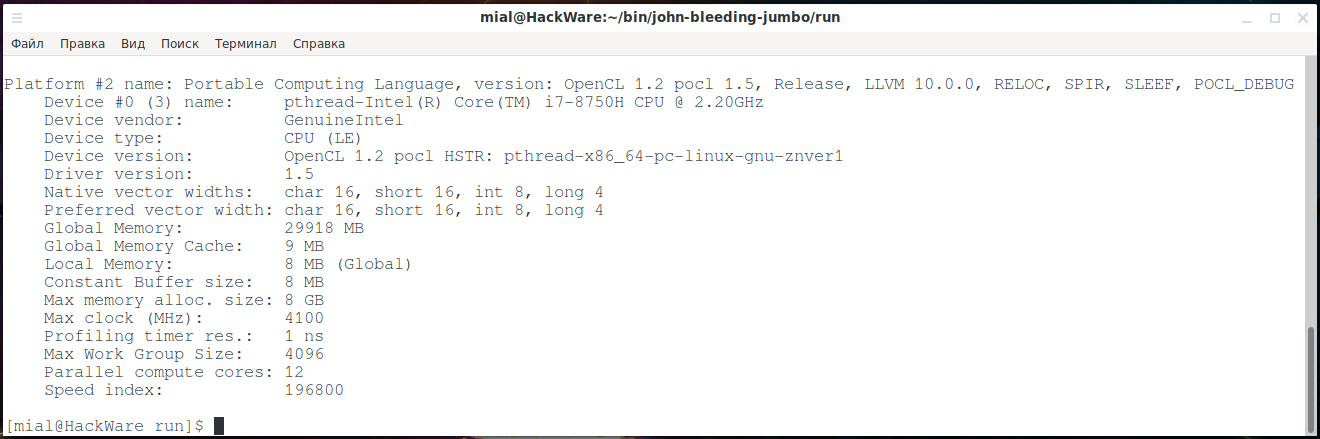
Comprehensive Guide to John the Ripper. Part 1: Introducing and Installing John the Ripper - Ethical hacking and penetration testing

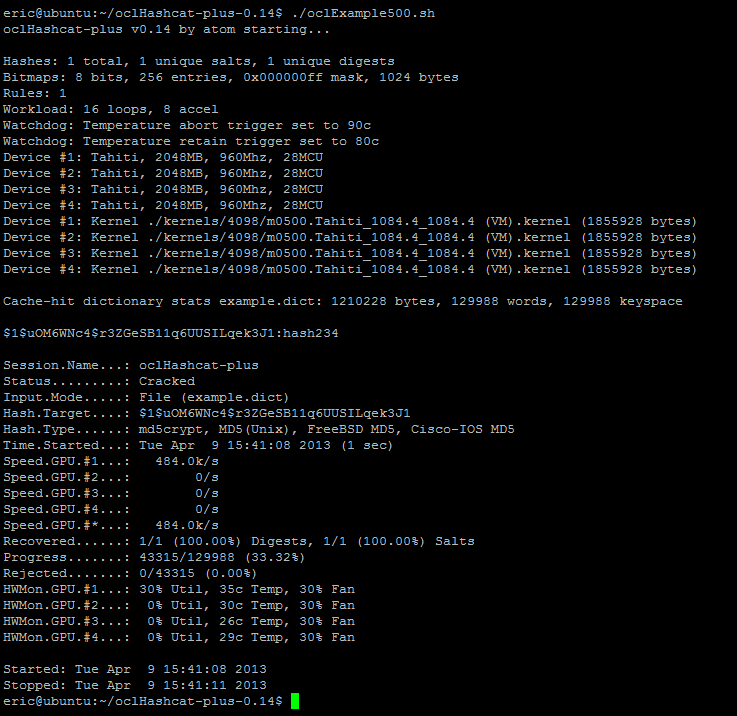
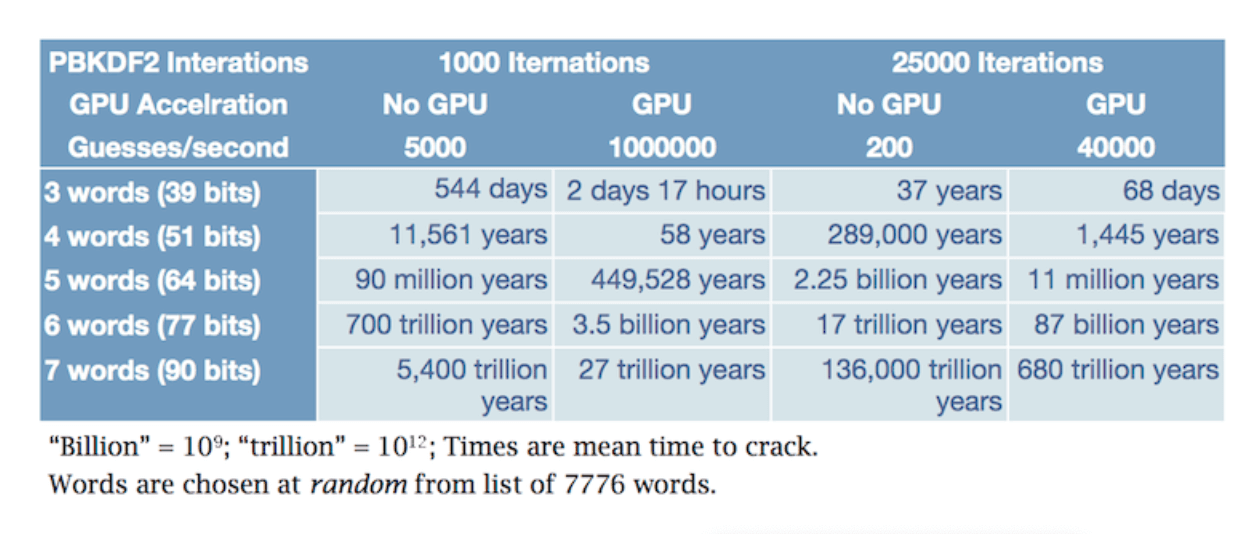
GPU Password Cracking – Bruteforceing a Windows Password Using a Graphic Card | Vijay's Tech Encounters
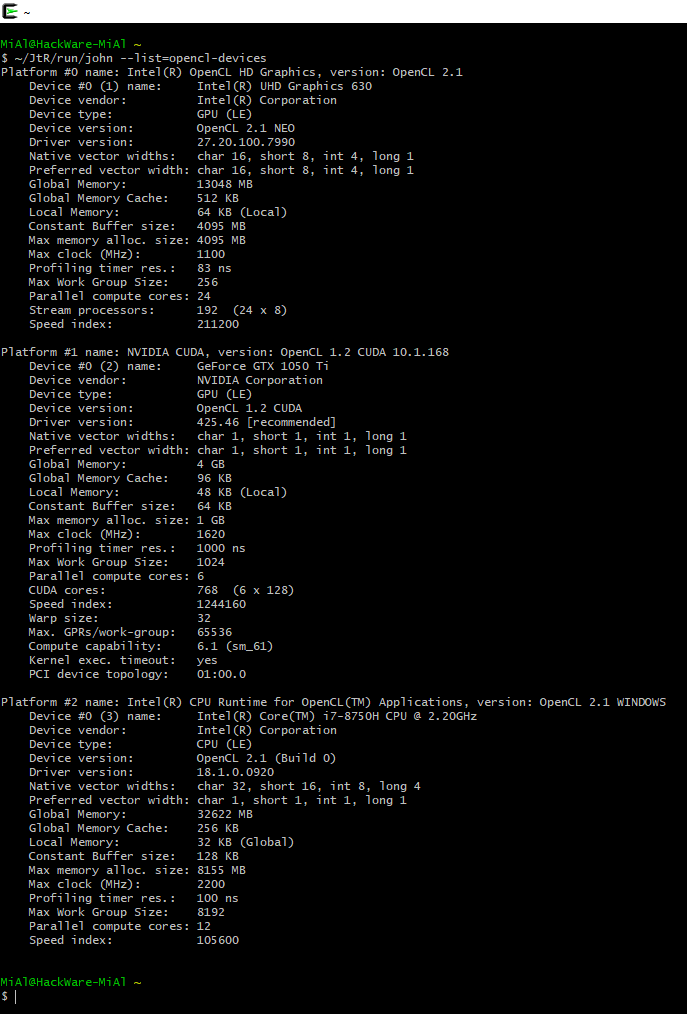
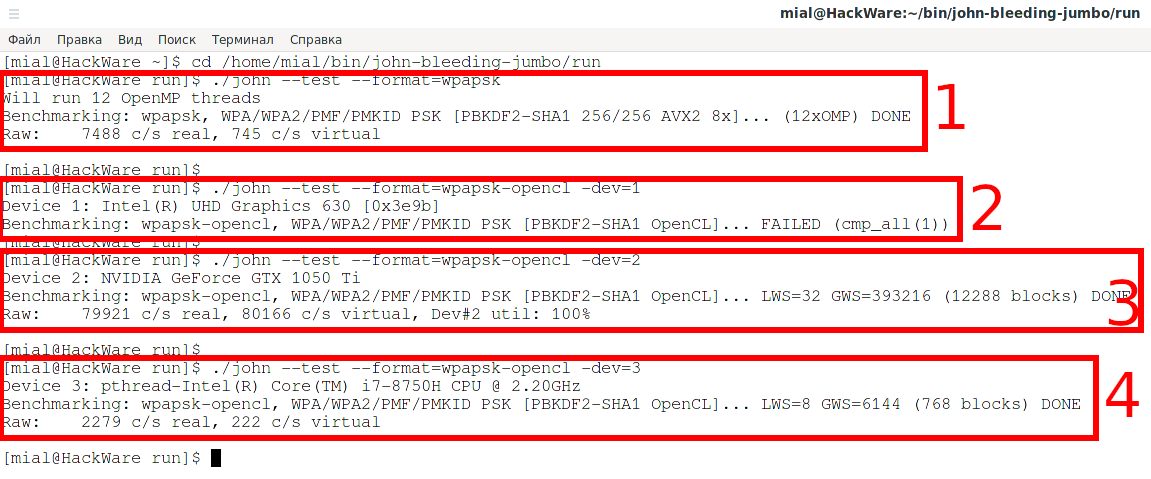
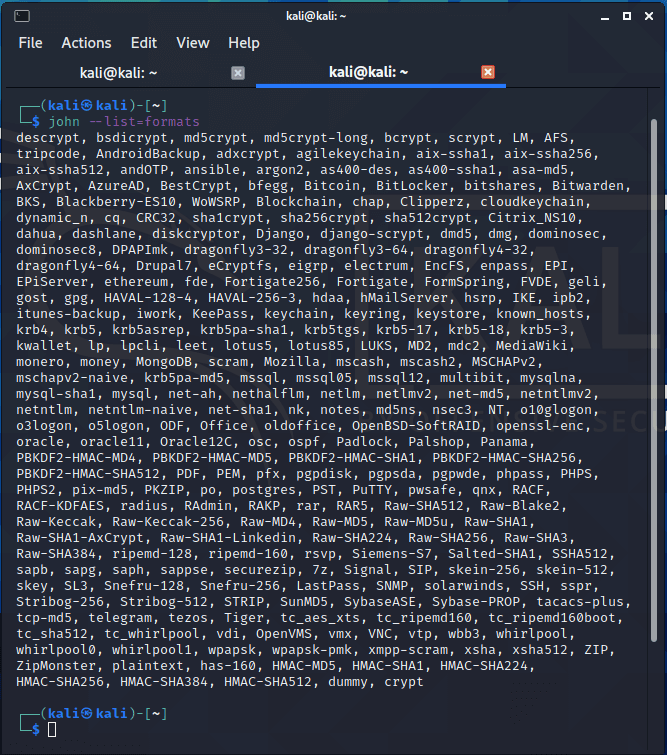
Comprehensive Guide to John the Ripper. Part 1: Introducing and Installing John the Ripper - Ethical hacking and penetration testing

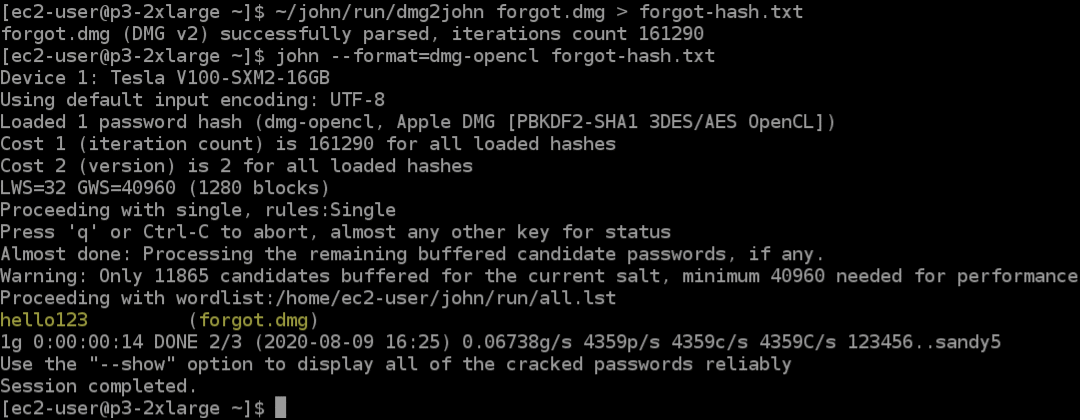
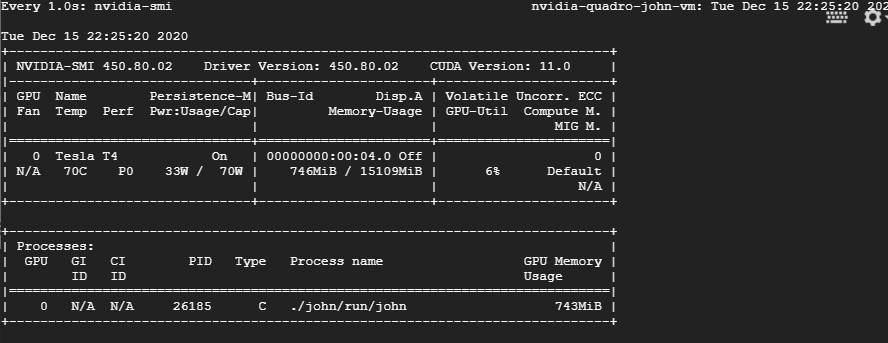
Comprehensive Guide to John the Ripper. Part 1: Introducing and Installing John the Ripper - Ethical hacking and penetration testing
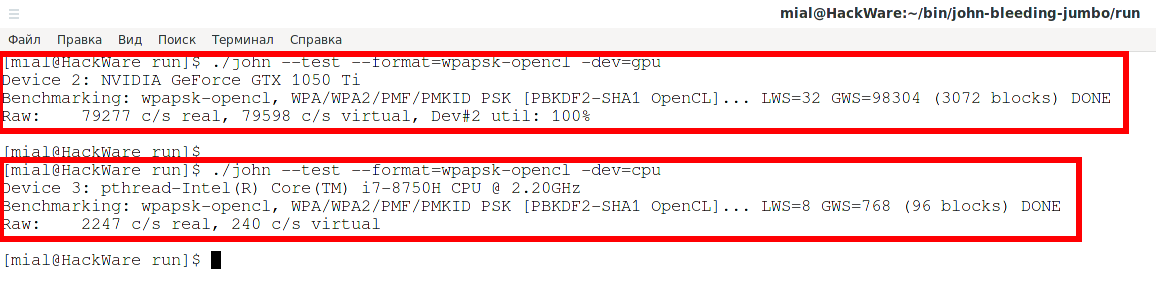
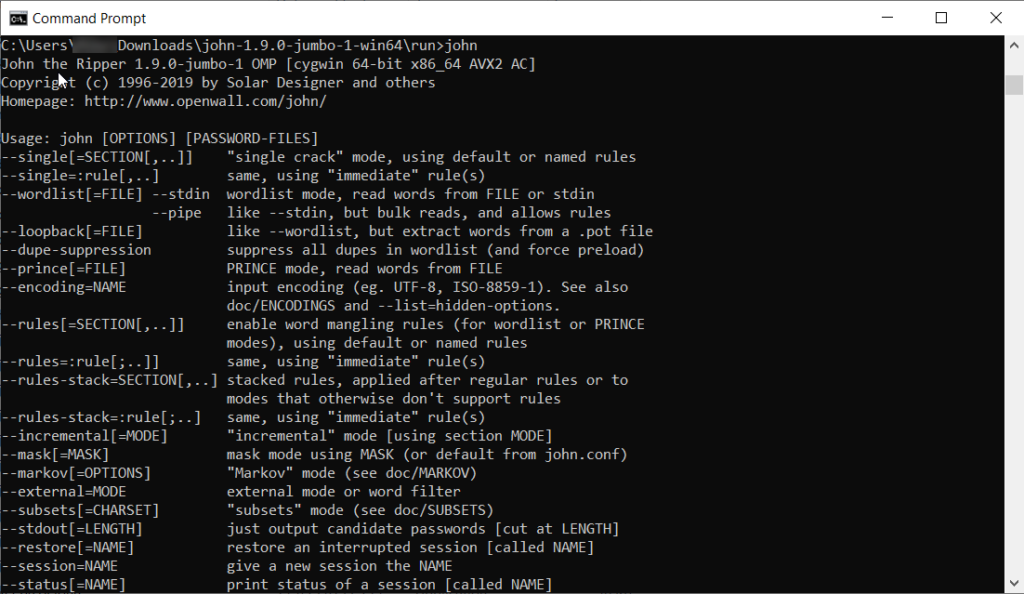
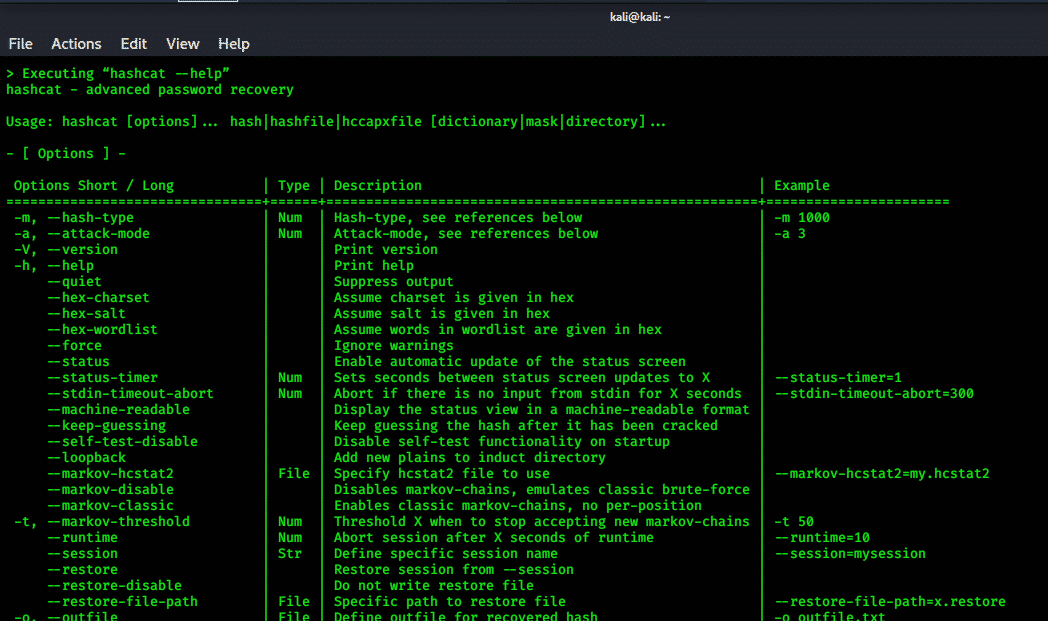
Comprehensive Guide to John the Ripper. Part 1: Introducing and Installing John the Ripper - Ethical hacking and penetration testing